8+ vector memory exhausted r
The structure of this document. Each rule guideline suggestion can have several parts.
Echtzeit Spektrumanalyse Software Aaronia Ag
JVM TI is intended to provide a VM interface for the full breadth of tools that need access to VM state.
. Assuming a array is created. These objects are referred to through symbols or variables. In the Settings search for Memory Settings and increase the IDE max heap size and Daemon max heap size as per the system RAM availability.
The GNU Arm Embedded Toolchain targets the 32-bit Arm Cortex-A Arm Cortex-M and Arm Cortex-R processor families. Various types of iterators are often provided via a containers interfaceThough the interface and semantics of a given iterator are fixed iterators are often implemented in terms of the structures underlying a container implementation and are often. You could try a sparse matrix instead which does not explicitly store all the 0s.
After calling this function the caller is responsible for the memory previously managed by the BoxIn particular the caller should properly destroy T and release the memory taking into account the memory layout used by BoxThe easiest way to do this is to convert the raw pointer back. Allocated memory contains an 8- or 16-byte overhead for the size of the chunk and usage flags similar to a dope vector. Cells Classical monocytes 158 2453 Effector memory CD8 T cells Exhausted B cells 31 33 Follicular helper T cells Intermediate monocytes 250 348 MAIT cells Myeloid dendritic cells 131 137.
This is driven by the convergence of various chronic signals including the antigen receptor and. It provides both a way to inspect the state and to control the execution of applications running in the Java TM virtual machine VM. Supported values of n are 2 3 4 8 and 16 for all vector data types.
Using electronic health records data from the All of Us Research Program we show that higher daily step counts in data collected over several years of Fitbit fitness tracker use were associated. To pick 8 numbers from 100 it is not necessary to create a array of 100 elements. The GNU Arm Embedded Toolchain is a ready-to-use open-source suite of tools for C C and assembly programming.
Has the power to doom this deal like it did. An Emperor from Barian World he manipulated Dr. Consumes the Box returning a wrapped raw pointer.
8 Single cell RNA-seq analysis using Seurat Analysis of single cell RNA-seq data. In computer programming an iterator is an object that enables a programmer to traverse a container particularly lists. Tag is the anchor name of the item where the Enforcement rule appears eg for C134 it is Rh-public the name of a profile group-of-rules type bounds or lifetime or a specific rule in a profile type4 or bounds2 message is a string literal Instruct.
What is the JVM Tool Interface. In computer science a stack is an abstract data type that serves as a collection of elements with two main operations. For clarity enabling technologies not disclosed with particularity in this Specification eg.
Pop which removes the most recently added element that was not yet removed. Orggradledaemontrue orggradlejvmargs-Xmx2560m Through GUI. Faker and Vetrix to fulfill his own ambition of destroying Astral World.
Anti-tumor immunity is limited by reduced T cell persistence and antigen presentation. Use gc to clear now unused memory or better only create the object you need in one session. Push which adds an element to the collection and.
The vector data type is defined with the type name ie. History of the issue. The nuclear program of Iran is an ongoing scientific effort by Iran to research nuclear technology that can be used to make nuclear weaponsIran has several research sites two uranium mines a research reactor and uranium processing facilities that include three known uranium enrichment plants.
This wastes memory resources and can lead to allocation failures when these resources are exhausted. A 67856 x 67856 matrix holds 46 billion 64-bit numbers meaning it would take over 32GB of memory just to store it. Keep all other processes and objects in R to a minimum when you need to make objects of this size.
Below memory size 1 can be configured based on the RAM availability. Show that Urolithin A a natural metabolite of pomegranate extract enhances antigen presentation in cancer and promotes mitophagy in CD8 T cells resulting in generation regenerative stem cell-like memory TSCM cells with enhanced anti-tumor properties. After his first defeat at the hands of Yuma Tsukumo Reginald Kastle and Kite Tenjo he orchestrated a new scheme by taking on a human form on Earth and calling himself Ray Shadows Rei Shingetsu in.
Downloads See Arm GNU Toolchain Downloads to access the latest release of the toolchain. The problem is not with creating such a matrix but fitting it into memory. Logical errors All allocations must follow the same pattern.
Add the below lines into the gradleproperties file. Memory heaps are either device-local or host-local but are always visible to the device. The pointer will be properly aligned and non-null.
1 man java. The length of one or more dimensions may be. A wireless ad hoc network WANET or mobile ad hoc network MANET is a decentralized type of wireless networkThe network is ad hoc because it does not rely on a pre-existing infrastructure such as routers in wired networks or access points in wireless networks.
There is good support in R see Matrix package for eg for sparse matrices. Irans nuclear program was launched in the 1950s with the help of the United States. 451 Subsetting by.
This is a implementation of Fisher YatesDurstenfeld Shuffle but without actual creation of a array thus reducing space complexity or memory needed when the pick size is small compared to the number of elements available. Where this Specification uses technical terminology defined in the Glossary or otherwise that refer to enabling technologies that are not expressly set forth in this Specification those enabling technologies are EXCLUDED from the Scope of this Specification. The transcriptome and epigenome of exhausted T cells suggest a distinct differentiation trajectory from effector and memory T cells 5 7 8.
Mannaggia Its not emphasized enough in this answer but whatlines should be a set because if i in whatlines will execute faster with a set rather than a sorted list. Additionally a peek operation can without modifying the stack return the value of the last element added. But the Xbox maker has exhausted the number of different ways it has already promised to play nice with PlayStation especially with regards to the exclusivity of future Call of Duty titles.
Char uchar short ushort int uint long ulong float or double followed by a literal value n that defines the number of elements in the vector. Device memory is explicitly managed by the application. Vector is a character in the Yu-Gi-Oh.
Unallocated chunks also store pointers. Each device may advertise one or more heaps representing different areas of memory. Instead each node participates in routing by forwarding data for other nodes so the determination of which nodes.
The JVM TM Tool Interface JVM TI is a programming interface used by development and monitoring tools. I didnt notice it first and instead devised my own ugly solution with sorted list where I didnt have to scan a list each time while if i in whatlines does just that but difference in performance was negligible. Questions about the nature of conscious awareness have likely been asked for as long as there have been humans.
Neolithic burial practices appear to express spiritual beliefs and provide early evidence for at least minimally reflective thought about the nature of human consciousness Pearson 1999 Clark and Riel-Salvatore 2001. R does not provide direct access to the computers memory but rather provides a number of specialized data structures we will refer to as objects. R ensures that the length of the vector is the product of the lengths of the dimensions.
Unless Microsoft is able to satisfy Sonys aggressive demands and appease the CMA it now looks like the UK. Further detail about memory heaps is exposed via memory types available on that heap.

Error Vector Memory Exhausted Limit Reached Guide To Fixing This
Frontiers Cd8 T Cell Response To Hiv Infection In The Era Of Antiretroviral Therapy
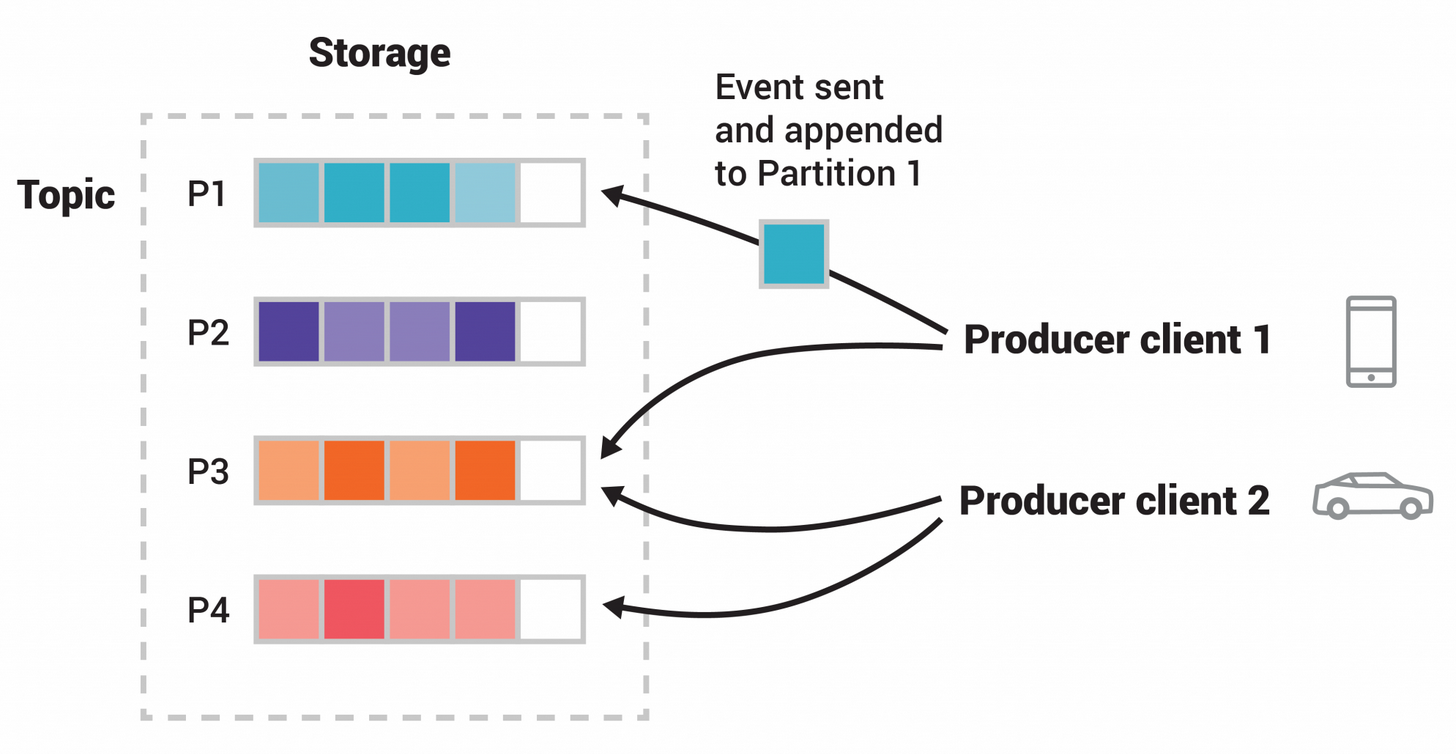
Apache Kafka

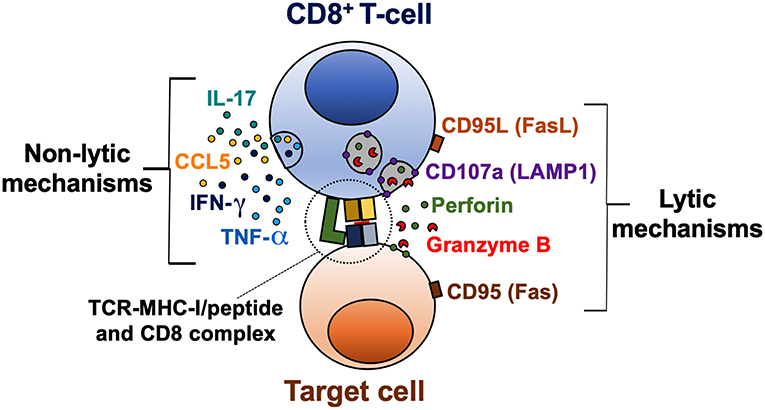
Cytotoxic T Cell Overview Thermo Fisher Scientific Us
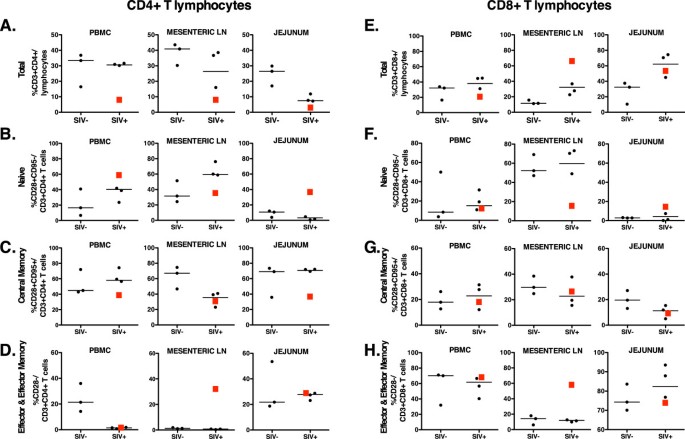
Prolonged Tenofovir Treatment Of Macaques Infected With K65r Reverse Transcriptase Mutants Of Siv Results In The Development Of Antiviral Immune Responses That Control Virus Replication After Drug Withdrawal Retrovirology Full Text

Error Vector Memory Exhausted Limit Reached Guide To Fixing This

Immunological Memory To Sars Cov 2 Infection And Covid 19 Vaccines Sette 2022 Immunological Reviews Wiley Online Library

Immune Checkpoints In Hematologic Malignancies What Made The Immune Cells And Clinicians Exhausted Hajifathali 2020 Journal Of Cellular Physiology Wiley Online Library

Understanding Idiosyncratic Toxicity Lessons Learned From Drug Induced Liver Injury Journal Of Medicinal Chemistry
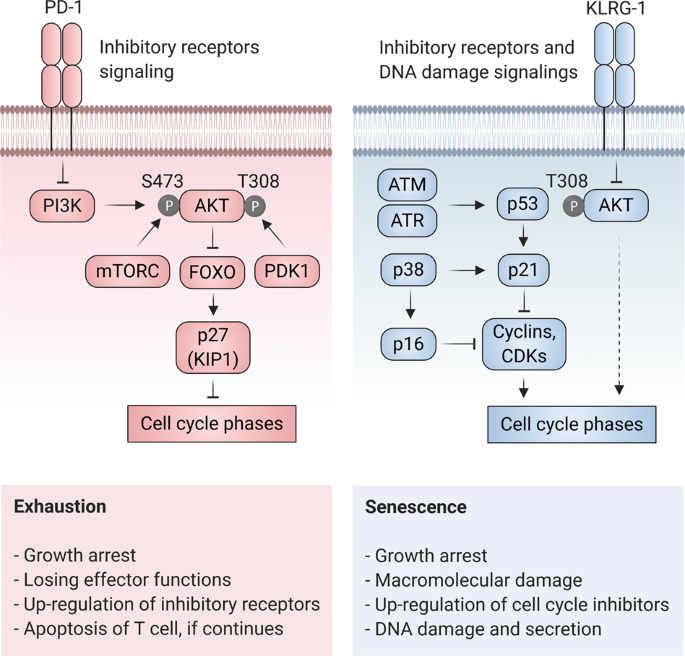
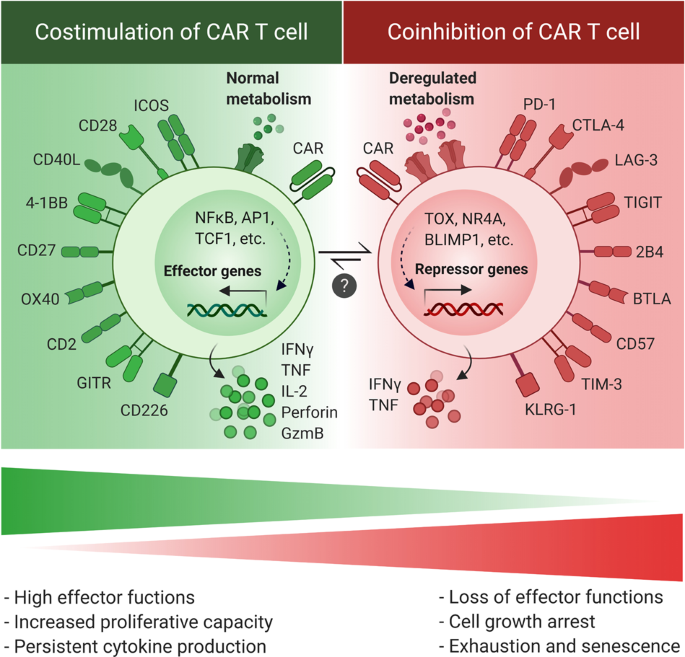
Counteracting Car T Cell Dysfunction Oncogene
Bsf Slovenian Film Database

Programmed Cell Death Protein Ligand 1 Silencing With Polyethylenimine Dermatan Sulfate Complex For Dual Inhibition Of Melanoma Growth Acs Nano
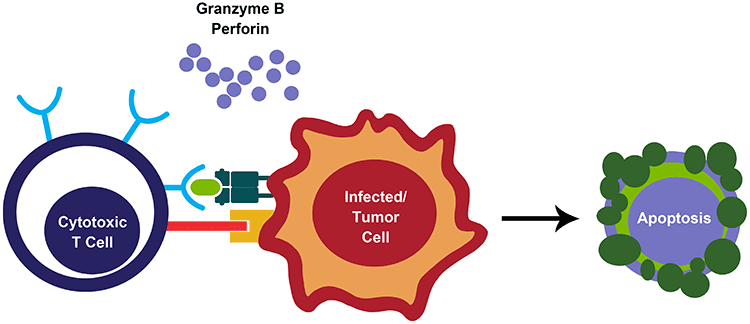
Cytotoxic T Cell Overview Thermo Fisher Scientific Us
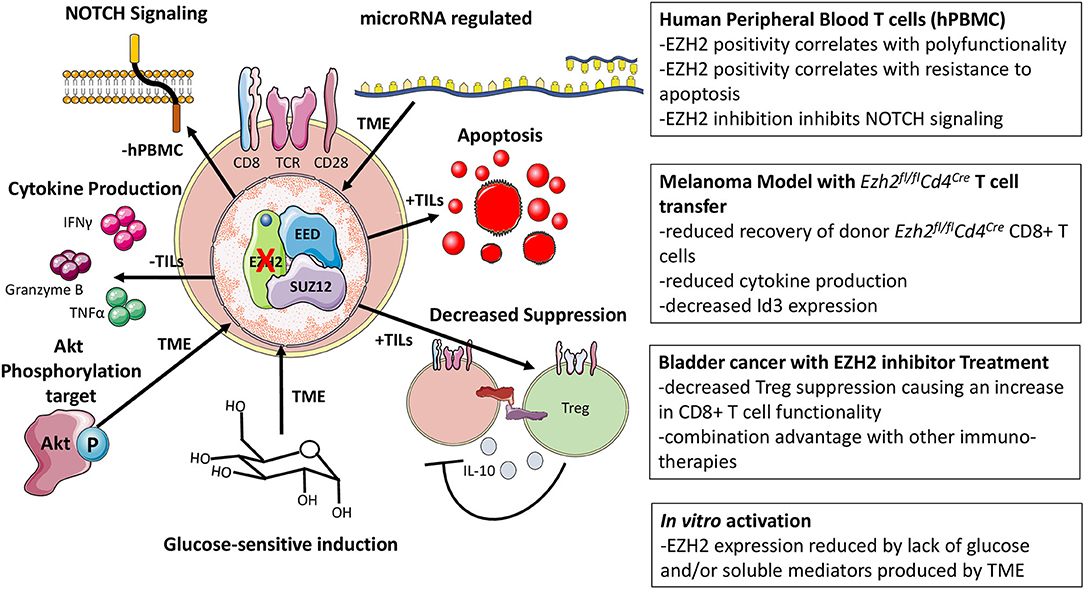
Frontiers Ezh2 As A Regulator Of Cd8 T Cell Fate And Function

An Adaptable Water Soluble Molecular Boat For Selective Separation Of Phenanthrene From Isomeric Anthracene Journal Of The American Chemical Society
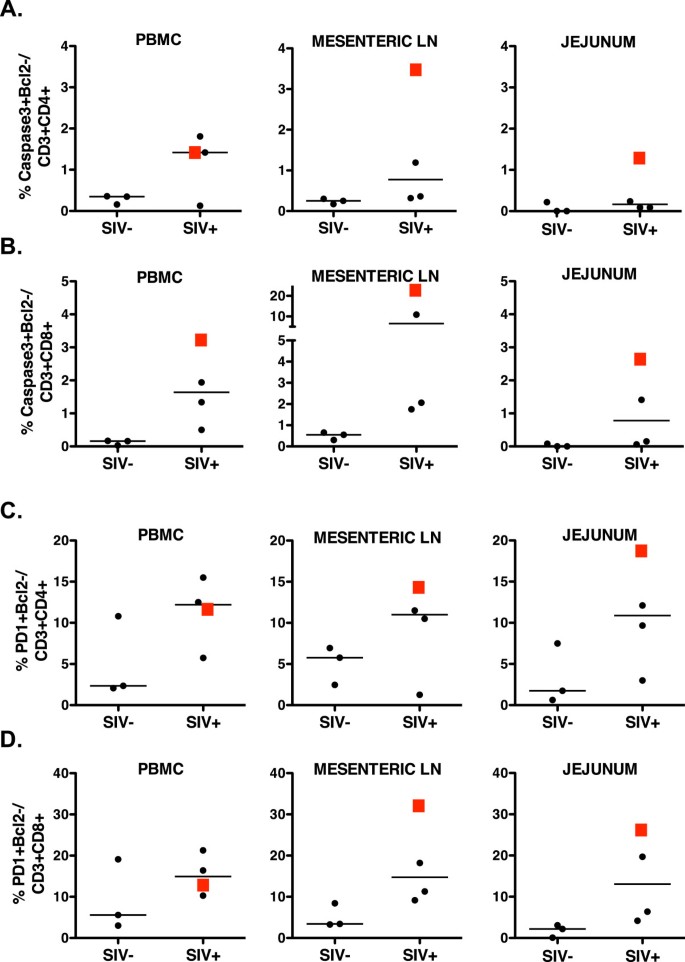
Prolonged Tenofovir Treatment Of Macaques Infected With K65r Reverse Transcriptase Mutants Of Siv Results In The Development Of Antiviral Immune Responses That Control Virus Replication After Drug Withdrawal Retrovirology Full Text

Immunological Memory To Sars Cov 2 Infection And Covid 19 Vaccines Sette 2022 Immunological Reviews Wiley Online Library